The first time I ran a security audit on an accounting website, I thought, “How bad could it be? These guys are all about details, right?” Cut to me, staring at a dashboard lit up like a Christmas tree, realizing that half the plugins hadn’t seen an update since Obama was in office. There’s nothing quite like the feeling of knowing you’re one click away from a ransomware headline.
If you’re running an accounting firm – or you’re the one responsible for its digital well-being, let’s face the music: you need to know this stuff because the odds are not in your favor.
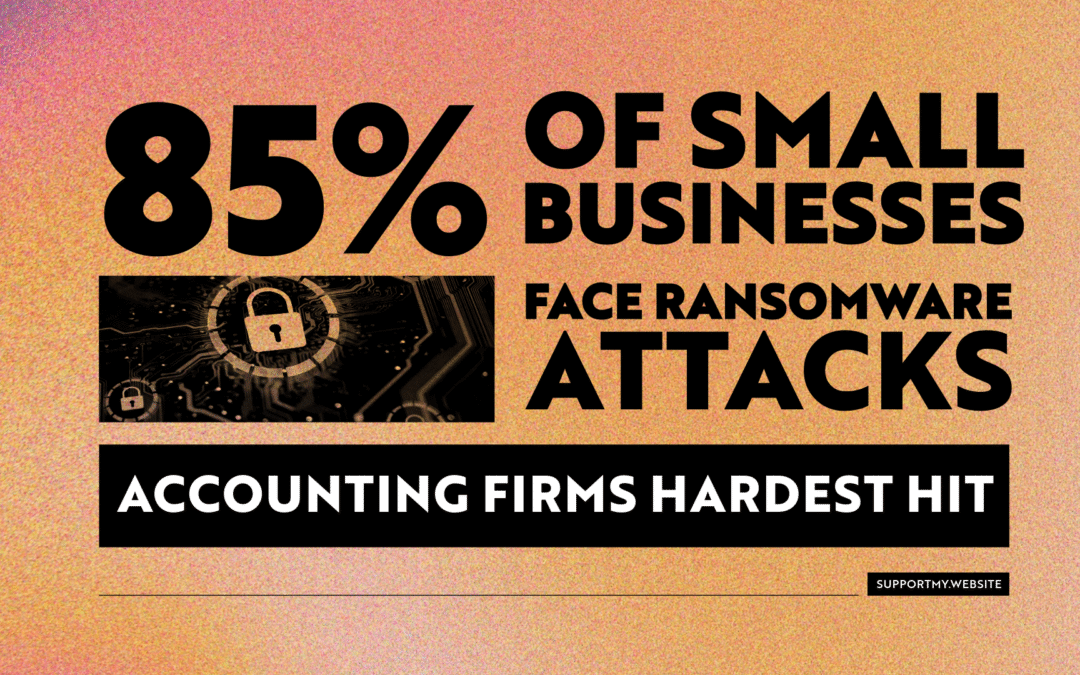
The Alarming Security Reality
Let’s start with the facts:
- 85% of managed service providers say ransomware attacks hit small and medium-sized businesses, with accounting firms “the most designated among small firms.” (CPAdirectory, 2024, citing CNBC)
- Human error? It accounts for 95% of all cyber breaches. (Security Magazine, 2024)
- 82% of ransomware attacks target companies with fewer than 1,000 employees. 37% hit companies under 100 employees. (StrongDM, 2025)
Why do the bad guys love accounting firms? In one word: data. You’re sitting on a goldmine of financial records, SSNs, tax documents – the kind of stuff hackers dream about on their off nights.
Here’s the promise: by the end of this article, you’ll know the seven ways most accounting firms fail security audits, what those failures really cost you, and a practical, step-by-step fix. And yes, there’s a downloadable checklist at the end – because no one needs another vague “best practices” post.
The Unique Security Challenges for Accounting Firms
The Data Jackpot
Let’s get specific. Here’s what makes your firm such a juicy target:
- Client financial info: Bank accounts, investment portfolios, payroll records.
- Tax documentation: SSNs, EINs, payroll data, W-2s, K-1s. (Basically, everything you’d need for identity theft, all in one place.)
- Business records: P&Ls, balance sheets, proprietary contracts, and vendor payment info.
If you think, “We’re just a local CPA, not a bank,” congrats – so did the last firm that got hit. (Ask any small firm in the CPAdirectory ransomware stats.)
Regulatory Headaches
It’s not just about the hackers. Compliance is a full-contact sport:
- IRS Safeguards Rule: Mandates security plans, risk assessments, and incident response (IRS Safeguards Rule).
- State CPA requirements: Vary, but always circle back to data protection and confidentiality.
- GLBA, SOX, and more: If you touch financial data, you’re on the hook.
You don’t just risk fines – your firm’s license, reputation, and client trust are all on the line.
Attack Vectors: Where They Get In
- Phishing: Tax season brings a 350% increase in phishing attempts aimed at accounting staff. (StrongDM)
- Ransomware: Targeted attacks spike during tax deadlines, when “just pay the ransom” feels like the only option.
- Client portals: Vulnerabilities here mean hackers get the keys to the whole kingdom.
Ever get a weird email from “QuickBooks Support” during tax season? You’re not alone. And if your staff can’t spot a fake, you’re already behind.
Key Takeaway:
Accounting firms aren’t just targets – they’re priority targets, with both hackers and regulators lining up for a piece. Pretending otherwise is a one-way ticket to the breach notification list.
Top 7 Security Audit Failures in Accounting Firms
Here’s the ugly truth: 73% of accounting firms fail their first real website security audit. Most don’t even know they’re failing until it’s too late.
Let’s walk through the most common tripwires – and how they blow up in practice.
1. Outdated Software and Plugins
Case in Point:
I once audited a firm running WordPress 4.x (three years out of date) with a dozen plugins flagged for “critical vulnerabilities.” They didn’t update because “the site still worked.” Spoiler: so did the exploit kits.
- WordPress/plugin update failures: Hackers actively scan for out-of-date plugins. It’s like leaving your office door unlocked and putting up a sign.
- OS security patches: If your web host isn’t updating, you’re a sitting duck.
- Third-party integrations: One outdated file transfer plugin = a direct pipeline to your client data.
Key Takeaway:
“If it ain’t broke, don’t fix it” is the official slogan of hackers everywhere.
2. Human Error and Training Failures
You can have the best firewall in the world – one click on a phishing email, and it’s game over. When I was the CEO at a healthcare tech company, we had sophisticated phishing attacks on the finance department weekly and unsophisticated attacks DAILY. (Remember: 95% of breaches are human error. Security Magazine, 2024)
- Training gaps: Most firms do “annual training” with a 40-slide PowerPoint. Staff forget 90% by Monday.
- Phishing exposure: Employees at small firms are 350% more likely to get tricked than those at Fortune 500s, especially in the finance and accounting functions of the business. (StrongDM)
- Passwords: “Spring2024!” is not a password. It’s a dare.
Pro Tip:
Run a simulated phishing campaign. If no one fails, you’ve either hired unicorns or they know the test is coming.
3. Inadequate Encryption Implementation
I’ve seen more unencrypted emails with client tax returns than I care to admit. If you’re still sending sensitive docs over plain email – or worse, storing them on a laptop with no disk encryption – brace yourself.
- Unencrypted emails: Easy pickings for “man-in-the-middle” attacks.
- No secure client portal: If your portal isn’t using HTTPS with a valid certificate, you might as well post the data on Reddit.
- Unencrypted devices: Lost laptop = breach notification (and a very awkward phone call to every client).
Key Takeaway:
Encryption isn’t optional. It’s table stakes.
4. Multi-Factor Authentication Gaps
Still relying on passwords alone? That’s like locking your front door but taping the key to the mailbox.
- Single-factor systems: Easy to brute-force.
- Shared admin logins: Every intern and temp has the “admin” password? Yikes.
- Weak session management: Sessions that never expire = risk that never goes away.
Pro Tip:
If your provider doesn’t offer MFA, it’s time to switch.
5. Backup and Recovery Failures
Backups are like parachutes: you only notice the quality when you need them.
- Unencrypted backups: Hackers love unencrypted files. They don’t even have to work for it.
- No backup verification: I’ve seen “backups” that turned out to be empty folders.
- Recovery testing: If you haven’t restored from backup in the last six months, you don’t have a backup – you have a wish.
Stat:
Average ransomware recovery takes 24 days (Varonis, 2024). Every day you’re down, the bill climbs.
6. Third-Party Vendor Security Oversights
You can do everything right – and still get burned by a vendor.
- Unvetted integrations: That “handy” payroll plugin might be a backdoor.
- No due diligence: Do you have a checklist for new vendors? Didn’t think so.
- Missing security clauses: If your contract doesn’t require vendor security, it’s not a contract – it’s a handshake.
Key Takeaway:
You’re only as strong as your weakest link – and in most firms, that’s a third-party vendor.
7. Remote Work Security Vulnerabilities
The pandemic broke the old perimeter. Now, your “office” is 14 home networks and a Starbucks Wi-Fi.
- Compromised home networks: Default router passwords are a gift to hackers.
- Personal device use: If your team is using their own laptops, you need mobile device management – yesterday.
- Unsecured remote access: RDP without VPN? That’s basically broadcasting your login to the world.
Pro Tip:
Assume every home network is compromised. Build your security plan from there.
The Real Cost of Security Audit Failures
You might think, “Okay, but how bad can it really get?” Brace yourself.
Direct Financial Impact
- Average cybersecurity incident cost (SMBs): $25,000–$826,000 (Business Dasher, 2024)
- Average ransomware recovery: $1.85 million (Varonis, 2024)
- Financial services breach: $6.08 million – 22% higher than the global average (IBM Cost of Data Breach, 2024)
If you’re running a tight-margin shop, even the low end of those numbers can be existential.
Regulatory and Compliance Nightmares
- IRS/GLBA fines: Non-compliance can mean five- or six-figure penalties (IRS Safeguards Rule).
- License issues: Some states will yank your CPA license for repeated violations (AICPA Regulatory Guidance).
- Legal/investigation costs: Breach notifications, lawsuits, and forensic audits are all billable – by someone else (FTC Data Breach Guidance).
Business Disruption and Long-Term Pain
- Average recovery time: 279 days (Business Dasher, 2024)
- 60% of small businesses close within six months of a cyber attack (PurpleSec)
- Reputation damage: Ever tried explaining to a client why their Social Security number was leaked? Not fun.
- Cyber insurance hikes: If you’re non-compliant, some policies won’t pay out (Insurance Journal).
Key Takeaway:
Ignoring security doesn’t just cost money – it can cost your entire business.
The Security-First Website Maintenance Framework
So, what actually works? Here’s the process we use at Support My Website – adapted for accounting firms.
Daily Security Monitoring
- Automated threat detection: Use a tool that scans for malware, suspicious logins, and file changes.
- Login monitoring: Track failed/successful logins. Alert on brute-force attempts.
- Malware scanning: Schedule daily (or more frequent) site scans.
Example tools: Wordfence for WordPress, or enterprise solutions like Sucuri. There are tons of solutions out there, so get someone who knows this stuff to help you.
Weekly Security Updates
- Software updates: Apply all CMS, plugin, and OS patches. No exceptions.
- Patch deployment: Prioritize critical security fixes.
- Vulnerability assessment: Use automated scanners (like Nessus or Qualys) to catch new risks.
Monthly Security Audits
- Comprehensive testing: Manual review of access controls, permissions, and change logs.
- Backup integrity verification: Restore a backup to a test environment every month.
- Access review: Remove ex-employees, update permissions.
Quarterly Security Reviews
- Penetration testing: Hire an outside firm to try breaking in.
- Security policy updates: Review and refresh your written policies.
- Staff training: Mandatory refresher sessions, with simulated phishing.
Key Takeaway:
Security isn’t a “set and forget” project. It’s a continuous process – daily, weekly, monthly, quarterly.
Implementation Action Plan
You know the problems. Here’s how to actually fix them – without losing your mind or your business.
Immediate Security Assessment
Step 1: Download the Accounting Firm Security Audit Checklist
(Or just grab the one at the end of this article.)
Step 2: Identify your top 3 vulnerabilities.
Don’t try to fix everything at once. Start with the biggest risks.
Step 3: Implement quick wins.
- Update all software/plugins.
- Enforce password changes.
- Turn on two-factor authentication.
30-Day Security Enhancement Plan
Week 1:
- Critical security updates
- Lock down admin accounts
- Enable encrypted backups
Week 2:
- Set up daily monitoring
- Review all vendor access
- Draft/update incident response plan
Week 3:
- Phishing simulation
- Mandatory staff training
- Mobile device management setup
Week 4:
- Test full site recovery from backup
- Schedule quarterly penetration test
- Review and sign vendor contracts
Ongoing Security Maintenance
- Monthly: Schedule audit, review logs, test backups.
- Quarterly: Penetration testing, full staff retraining.
- Ongoing: Monitor alerts, respond to incidents immediately.
Key Takeaway:
Don’t wait for a breach to build your plan. Start today, or you’ll be planning your apology tour tomorrow.
Content Assets
- Security Audit Checklist for Accounting Firms
- Vulnerability Assessment Worksheet
- Security Incident Response Template
- Staff Training Checklist
(Hint: If you want these in ready-to-go spreadsheet or template format, just reply and I’ll send them over.)
Rapid-Fire Takeaways
- Accounting firms are hacker catnip. You’re swimming in valuable data.
- The cost isn’t just financial – it’s existential. Most small firms never recover.
- Proactive, scheduled security is the only answer. Daily, weekly, monthly, quarterly.
- You can fix this today. With the right framework and a little sweat.
Action Steps
- Download the security audit checklist and run a self-assessment this week.
- Update all software and enable MFA – the easiest, highest-impact fixes.
- Schedule a team training and phishing simulation before next month.
Invitation
Got a horror story or a question? Want the templates or a free website security audit?
Reply here, reach out on LinkedIn, or hit the contact form at Support My Website.
I read every message. And I’ve been there. Let’s make sure you don’t have to go through it alone.

Jason Long
Jason is a serial problem solver and entrepreneur with 20+ years of experience in business building.
Jason’s ventures range from agriculture to healthcare with a focus on web-based technology. He has extensive experience in software development and has operated as a developer, UX designer, graphic designer, project manager, director, executive coach, and CEO.
Linkedin
Personal Website
Sources:
- CPAdirectory, 2024, citing CNBC
- Security Magazine, 2024
- StrongDM, 2025
- Siccura, citing Dark Reading
- Varonis, 2024
- IBM Cost of Data Breach, 2024
- Business Dasher, 2024
- PurpleSec
- Support My Website Security
- IRS Safeguards Rule
- AICPA Regulatory Guidance
- FTC Data Breach Guidance
- Insurance Journal
Note: If you need direct access to any checklist or template mentioned, let me know and I’ll make sure you get them!